Information Security
Information Security is concerned with protecting the confidentiality, integrity, and availability of... View more
How to Protect Your Business From the Dark Web [Updated]
-
How to Protect Your Business From the Dark Web [Updated]
You’ve probably heard about the Dark Web as a notorious center for criminal activity. Using applications like Tor, hackers can gain access with total secrecy and launch attacks with minimal technical expertise. However, if you’re looking for ways to prevent dark web attacks, there are several key steps you can take.
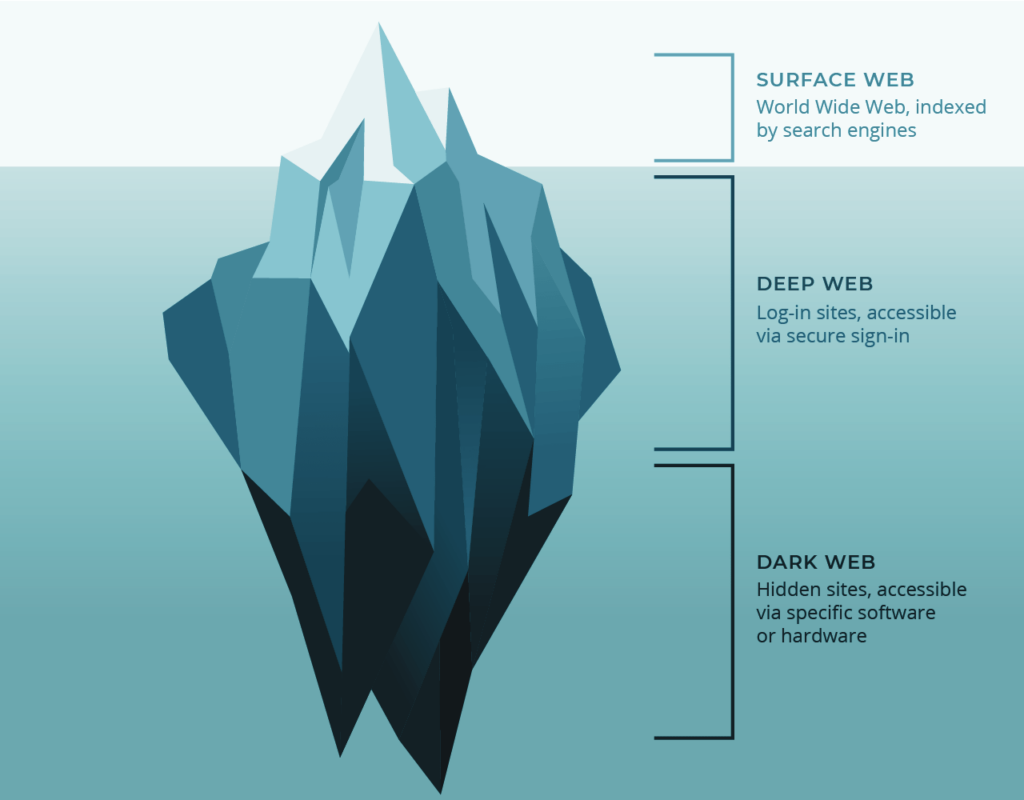
Know what the Dark Web is
The dark web is a place where cyber criminals gather and commit crimes. Over the last three years, the dark web has been the scene of a staggering amount of identity theft and fraud. Since March 2020, taxpayers have lost $63 billion in identity theft alone. Similarly, consumers have lost $370 million in scams involving Coronavirus. Luckily, there are a number of ways to protect yourself from these threats. One way is to download a fraud prevention package like iDenfy shield.
The Dark Web has a reputation for being a hotbed of criminal activity, but that does not mean that every single site on it is illegal. Many users use the dark web to trade goods and services. They can access these sites with the anonymizing browser software Tor. This way, they can sell their goods or services without the risk of being detected.
The dark web is an area of the internet that is not searchable by traditional search engines. It is only accessible with the use of specialized web browsers, such as Tor. It is also a site where criminals operate with complete anonymity. Some cybercriminals use the dark web as a conduit for illicit activities, including drug trade, human trafficking, and weapons dealing.
To combat dark web crime, law enforcement agencies must become more actively involved in investigating the crimes on the dark web. By investing in proper funding, hiring computer scientists, and training, local agencies can combat the problems in their respective communities. In addition, local leaders must support this initiative, which is intended to send a strong message that the dark web is not a safe haven for criminals.
The dark web can be an excellent source of intelligence, but failure to monitor this network can be a major risk for your organization. Many of the criminal sites on the dark web are not necessarily illegal, but many popular websites operate through it. Moreover, if you have personal information that has been compromised, it may be sold on the dark web. This means that criminals can steal it and sell it without you knowing it.
Use applications like Tor for secrecy
Tor is an anonymous network service that allows you to create anonymous websites and access them without revealing your real identity. These websites are also known as ‘dark websites’ because they are only accessible through complex Tor routes. These routes are run by volunteer nodes that are controlled by unknown people, but malicious entities can monitor them.
Tor uses a small network of redundant onion routers to track changes in the network topology and node state. Each of these routers is configured to be a directory server, acting as an HTTP server. Clients can fetch this state information from them, and other onion routers upload the same information. Each onion router regularly publishes signed statements of its state to directory servers, which combine those statements with their own views to generate an encrypted description of the network’s state. The client software bootstraps its view of the network by loading a list of these directory servers.
Applications like Tor are designed to be low-latency and easy to deploy. This frustrates attackers who seek to link multiple communications. Despite its low-latency nature, Tor has undergone significant changes over the years to become a more flexible, reliable, and cost-effective system. These changes are designed to make Tor more usable while preventing users from creating a huge liability burden on operators.
Tor is a browser that uses onion-like encryption to encrypt messages. Data is sent from one onion router to another until it reaches its destination. This slows down the speed of the dark web, but it ensures the security of users’ data.
While Tor promises total secrecy on the Dark Web, it has some drawbacks as well. It can be vulnerable to hackers and law enforcement officials. The only way to be sure that your privacy remains secure is to be very careful. The internet is full of cybercriminals and hidden services. If you do not protect yourself, you will be victim to their attacks.
Dark web users should also make use of privacy-search engines, such as DuckDuckGo. This search engine allows you to edit dark web pages anonymously without revealing your identity. The most popular dark web email service is ProtonMail. This is a secure and anonymous email service, which is ideal for registering on onion sites.
Know the risks and guard against them
Users of applications like Tor must be aware of the fact that malware can infect their devices through their browsers. One malware found in use was named OnionDuke. It is known to have ties to the Russian APT and was distributed by threat actors through malicious exit nodes. Malware is often disguised as a legitimate executable to circumvent security systems. In addition, malware can track users across different websites, including Tor exit nodes.
However, the dark web has proven to be an invaluable resource for activists and dissidents, as it provides them with an avenue to communicate with one another and bypass local restrictions. In addition, it serves as a critical tool for whistleblowers, as it shields them from judgment or retribution. The dark web also provides the anonymity and privacy that users seek. In fact, many organizations and individuals maintain a hidden website on Tor in order to demonstrate their commitment to maintaining anonymity and privacy.
Unencrypted data is vulnerable to capture by Man-in-the-Middle attacks. The attackers behind these attacks often target the default account, which has full administrative permissions. Therefore, users should limit access to this account to only those who need it.
Tor also exposes corporate networks to malware infections. In some instances, employees can access criminal Dark Web forums by bypassing the corporate network security. Furthermore, users may even have access to confidential information that could expose their company. The biggest risk that applications like Tor poses is a cyber-insider attack, where employees sell confidential information to third parties for insider trading or business intelligence.
Employers can help mitigate Tor risk by training employees about the risks it poses to corporate networks. They can also develop a blacklist of Tor nodes to block outbound traffic from the Tor network. This blacklist will prevent outbound Tor connections and provide a log of all Tor connections. However, it is important to remember that a blacklist must be maintained in order to remain relevant.
While Tor offers a solution to these problems, users should be aware of the risks associated with it. As with all Internet technology, organizations must assess the risks associated with new tools and services. To protect information assets, it is essential to evaluate the risks of new technologies. Applications like Tor can not only provide legitimate anonymity, but they can also expose corporate networks to malware and other malicious sites.
Be careful of what information you put out there on the internet
The internet has become a tool that cybercriminals can use to target specific targets. These victims may have responded to an ad or email or have accidentally downloaded malware. In other cases, they may simply have crossed paths with the criminal and come into contact with them. Regardless of the means by which they obtain the victim’s information, cybercriminals will still be able to launch a successful attack.
Cybercriminals can attack websites, systems, and databases using a variety of methods. They can take advantage of vulnerabilities in your operating system to distribute malicious software. This means that they can launch attacks with little technical knowledge. Most attacks rely on the user’s actions to download the malware, which may include clicking on a link or opening an attachment.
The goal of cybercrime is to compromise the security and confidentiality of a system, network, or data. The methods used by cybercriminals include hacking, malware creation, and malware possession. Many cybercriminals also target specific websites where people enter credit card information. This means that they will be tracking these websites, stealing data, and causing damage.
Social engineering is a simple but effective way for cybercriminals to gain access to your systems. They may target you based on a past relationship. They may stalk you on social media to threaten or coerce you into providing your information. They may also target a company because they have a particular ax to grind. They might be disgruntled employees or people who seek revenge.
Malware is a form of malicious software that can take control of your computer and send confidential data to cybercriminals. It can even pop up with malicious email attachments. Malware is the most common type of cyberattack, and it has many subtypes. Some of the most common malware types include viruses, worms, spyware, and ransomware.
Sorry, there were no replies found.