Information Security
Information Security is concerned with protecting the confidentiality, integrity, and availability of... View more
Dark Web vs Deep Web – 5 Key Differences You Must Know
-
Dark Web vs Deep Web – 5 Key Differences You Must Know
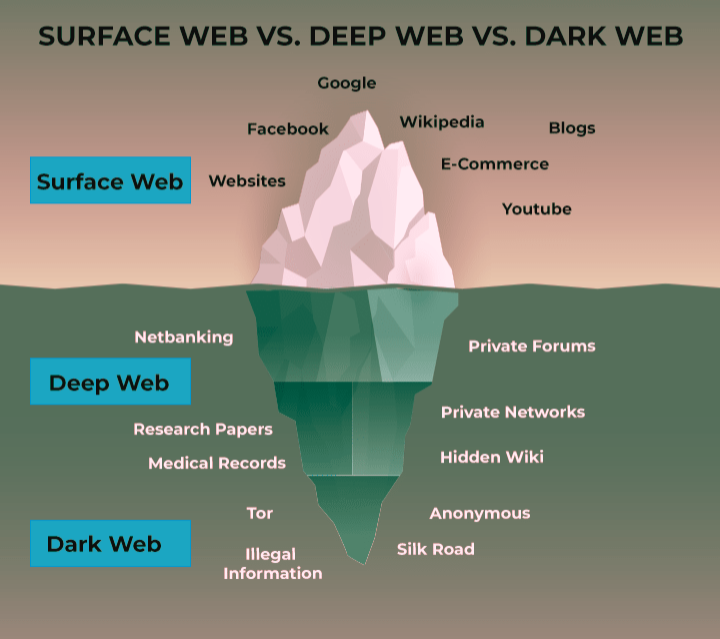
The term “Deep Web” is used to define the web section that isn’t indexed through web browsers. Dark web, on other hand, is described as a subset of the deep web that is only accessed with specific tools. The former is used mostly for everyday online activities while the latter is more private and is known for illegal transactions. This article highlights the top five major distinctions between the deep web and the dark web.
Dark Web vs. Deep Web
The deep web is a section of the internet that cannot be indexed by web crawlers. The dark web is a sub-segment of the deep web that can only be accessed with special tools, such as the Tor browser.
What Is the Dark Web?
The dark web is a subsection of the deep web including websites that one can only access through purpose-built web browsers. Some estimates mark the extent of the dark web as being much smaller than that of the surface web (which is the regular internet we use every day). However, it is challenging to measure how widespread the dark web is due to its decentralized and obscure nature.
Very few regular users will ever interact with the dark web. While the deep web usually requires just a username and password to be accessed (think of your email inbox), the dark web cannot be reached without the right software or hardware.
The architecture of the dark web features some key elements that make it an anonymous sanctuary for censured activities.
- Due to their unique registry operator, websites on the dark web are inaccessible by regular web browsers such as Google Chrome and Mozilla Firefox.
- Web crawlers cannot index the content hosted on the dark web. Network security tools such as encryption and firewalls prevent these search tools from discovering these websites.
- Access to dark web content is restricted with the help of virtual traffic tunnels through randomized network architecture.
The layman associates the dark web with illegal content and criminal activities such as trading illicit products and services. While this is mainly true, this online framework also has applications for legitimate entities. For instance, journalists in autocratic nations can use the dark web to pass information to their colleagues in other parts of the world.
The dark web was originally a domain exclusively used by cybercriminals and governments. Today, this is no longer true–advanced encryption technologies have made the anonymization of web surfing a hassle-free affair for regular users. The Tor browser is a popular tool for accessing the dark web.
Most enterprises do not have a direct use case for the dark web. However, cybersecurity organizations could benefit from indirect participation in discussions regarding hacking and exploit trading that regularly takes place on the dark web. This would give them insights into yet-unknown vulnerabilities and allow them to gain knowledge of exploits before they can turn into widespread cyber threats.
What Is the Deep Web?
Unlike the dark web, which is deliberately obscured by layers of technology, the deep web exists just below the surface web. The majority of the deep web consists of regular websites that require users to create an account before they can be accessed.
If the surface web is the visible part of an iceberg above water, the deep web is the part submerged beneath – much larger but hidden from plain view. Some people use the terms ‘dark web’ and ‘deep web’ interchangeably; however, significant portions of the deep web are completely legal and safe to use.
A majority of the web consists of databases and intranets. The former includes privately protected file collections that one cannot access without the correct credentials. The latter includes internal networks for governments, educational facilities, and corporations. The ‘members only’ parts of public platforms are also a part of the deep web.
All web pages not indexed by web crawlers are considered to be a part of the deep web. The content is generally more secure and clean than that of the surface web. This is because deep web content is usually well-maintained. Security tools such as firewalls help in this endeavor.
Simple examples of deep web content include financial data, social security databases, email inboxes, social media, medical documentation, legal files, blog posts that are pending review and web page redesigns that are in progress. These pages are mostly obscured from the surface web to secure user data and privacy rather than any nefarious purpose.
However, the deep web is not entirely devoid of danger. Some portions of the deep web allow users to overcome legal restrictions to access content that is not lawfully available in their geographical location. It is even possible to illegally download movies, music, and other digital media without paying for it. Naturally, these lawless segments of the deep web are rife with malware and other cyber threats.
While the content on the dark web has the potential to be more dangerous, this content is usually walled off from regular users. However, it is entirely possible for regular users to accidentally come across harmful content while browsing the deep web, which is much more easily accessible. This makes deep web security important for individuals and enterprises alike.
5 Key Differences Between the Dark and Deep Web
The terms dark web and deep web are perceived to be linked with illegal and otherwise suspicious activity; however, a vast difference exists between the two.
Outlined below are the top five differences between the dark and deep web:
1. Scope and Operations Dark Web Deep Web As a subsection of the deep web, the dark web cannot be indexed by web crawlers. However, there is an important difference: while the deep web content does not show up in the search results list, it is otherwise safe and can be accessed with a normal web browser.
On the other hand, one cannot visit the dark web without purpose-built software. This is because the dark web is placed on darknets, an overlay network that exists ‘on top of” the regular internet.
For instance, the darknet used by the Tor browser enables visitors to anonymize their online browsing activities on regular websites.
Apart from this, Tor allows users to access URLs ending with .onion through its ‘hidden services’ functionality. Users need this browser to access this special category of websites.
Tor makes hosting a website on the dark web simple. The anonymity offered by Tor allows both hosts and users to cloak their identities. By setting up the server correctly, hosts can even mask the location of their servers.
Using Tor, websites hosted on the dark web can only be viewed by visitors connected to the Tor network. Therefore, this content is inaccessible to most online users, and it is difficult to track the visitors of such websites.
Theoretically speaking, it should be impossible to locate dark web servers and track visitors. However, in practice, security flaws in Tor and incorrect server configurations can expose this information to those interested in accessing it.
Tor’s hidden services are not the only darknet service. Other options exist, but they are generally created to fulfill specific purposes, such as file sharing.
The deep web is much broader in scope than the dark web. This umbrella term covers all the parts of the online world that are not accessible by web search engines such as Google, Yahoo, Bing, or DuckDuckGo. Unlike the dark web, which majorly hosts content that is illegal or otherwise restricted in nature, the deep web hosts a wide range of material. The pages on the deep web can include paywalled websites, pay-to-access services such as Netflix, private databases, email mailboxes, and any other content that is not indexed by web search engines.
It is tremendously more vast than the surface web, with some experts estimating that search engines index less than 1% of online content.
Many websites on the deep web avoid showing up in search engine results by blocking the bots that ‘crawl’ the internet to collect information for search engine indexes.
Examples of deep web content include innocuous material such as emails, chat conversations, e-banking data, private posts on social media platforms, and electronic health records. This content is generally protected by credentials, commonly a username and a password.
In fact, unlike the dark web, the deep web is not hidden because it is malicious. It is simply a matter of privacy and relevance; users are less likely to find private databases (such as student records) useful in their day-to-day activities. Nobody wants their private emails to be seen by others with just a few clicks.
However, the deep web can also host illegal content such as pirated media. Anyone can access this material without needing a different web browser such as Tor.
2. Size Dark Web Deep Web The dark web technically speaking, is a subsection of the deep web. However, there is no true way to gauge how vast and deep the dark web truly is.
Some experts peg the size of the dark web at approximately 5% of all the content on the internet.
The deep web is much broader in scope than the dark web. This umbrella term covers all the parts of the online world that are not accessible by web search engines such as Google, Yahoo, Bing, or DuckDuckGo. Unlike the dark web, which majorly hosts content that is illegal or otherwise restricted in nature, the deep web hosts a wide range of material. The pages on the deep web can include paywalled websites, pay-to-access services such as Netflix, private databases, email mailboxes, and any other content that is not indexed by web search engines.
It is tremendously more vast than the surface web, with some experts estimating that search engines index less than 1% of online content.
Many websites on the deep web avoid showing up in search engine results by blocking the bots that ‘crawl’ the internet to collect information for search engine indexes.
Examples of deep web content include innocuous material such as emails, chat conversations, e-banking data, private posts on social media platforms, and electronic health records. This content is generally protected by credentials, commonly a username and a password.
In fact, unlike the dark web, the deep web is not hidden because it is malicious. It is simply a matter of privacy and relevance; users are less likely to find private databases (such as student records) useful in their day-to-day activities. Nobody wants their private emails to be seen by others with just a few clicks.
However, the deep web can also host illegal content such as pirated media. Anyone can access this material without needing a different web browser such as Tor.
3. Access Dark Web Deep Web Users cannot ‘accidentally’ access the dark web. Even if a cyberattack targets a user, it would be unlikely for the attack to have directly originated from the dark web. The tools to carry out the cyberattack may have been bought off a dark web marketplace, but the attacker would propagate the attack using mediums available on the standard web (such as email or chat).
Entry to the dark web is restricted intentionally. Special tools–the Tor Browser or the Invisible Internet Project (I2P) network–are needed to overcome these obstructions.
‘The Onion Routing’ (Tor) is a project that has led to the creation of the Tor browser, making it easy for even regular web users to visit the dark web. This web browser enables users to see URLs hosted by the ‘. onion’ registry operator.
Interestingly, at the cusp of the new millennium by the US Naval Research Laboratory originally developed the Tor project. An early version of the Tor browser was created to combat the challenges presented by the lack of privacy during the initial days of the internet. Its main goal was to prevent spy communications from being discovered; however, the framework was eventually repurposed and made public.
Using Tor to access the dark web is not particularly difficult. Operating Tor is largely similar to operating a web browser such as Mozilla Firefox or Google Chrome.
However, Tor does not establish a direct connection between the user endpoint and the internet. Instead, it passes user data through a randomized link of encrypted servers called nodes.
This connection methodology enables users to interact with the dark web with minimal risk of their activity being tracked or otherwise exposed.
No filters between users and the deep web. Any user with an internet-enabled device and the correct set of credentials can access a website on the deep web. Most internet users access the deep web almost every time they are online.
From the login page of internet service providers to email mailbox or even social media profiles, are a part of the deep web.
It is worth noting that some pages on the deep web contain valuable personal data to cybercriminals. Securing this data prevents it from being compromised and possibly showing up for sale on the dark web.
4. Applications Dark Web Deep Web The main application of the dark web is to provide anonymity to both website owners and visitors. The dark web helps obscure websites that do not wish to be on the regular internet, where they could be monitored.
This anonymity is not necessarily used exclusively for illegal activity. For instance, political dissidents under an oppressive government might use the dark web for communication.
The dark web may also be put to good use by whistleblowers, who can leak classified information on the dark web using websites such as Wikileaks. Using the dark web decreases the chances of them being caught.
Interestingly, even Facebook can be accessed as a Tor-hidden service, allowing users in countries with no legal access to its platform to visit the website safely.
However, this anonymity also has its drawbacks. It enables people to host websites selling illegally-obtained credit cards and social security numbers, counterfeit money, forged documents, weapons, and drugs and is even used for criminal activities.
Payment for these services is generally made using difficult-to-trace digital currency, such as Bitcoin.
As discussed above, the deep web is visited regularly by most internet users. Listed below are three key applications of the deep web: Intranets, or internal networks used by companies and academic institutions, cannot be accessed by the public. They require access to a specific VPN service and credentials before they can be viewed. Organizations use intranets for internal communication and documentation and for hosting internal online tools.
Subscription-based applications can be accessed only once the user has paid for them. The paywall prevents search engine crawlers from accessing this content. Examples include software as a service (SaaS) solutions, paid news websites, and streaming services.
Even free online services that are open to the public can be categorized as part of the deep web. For instance, banking websites require users to log in before viewing their account statements. Even email services such as Gmail are part of the deep web, as search engines cannot access the data on the platform.
5. Security Dark Web Deep Web The dark web is constantly evolving, with new marketplaces and forums for criminal activity cropping up frequently. Organizations are at risk of data theft by cybercriminals. Stolen data often ends up on the dark web for sale, giving cybercriminals the incentive to target organizations with sensitive customer data (such as financial institutions).
This illegally-obtained data can allow malicious actors to gain access to confidential data, use stolen credit card numbers, and even bring down the entire remote infrastructure of an enterprise.
Disregarding dark web security can lead to irreversible damage to an enterprise’s reputation, besides heavy monetary losses.
By monitoring the dark web, security teams can gain information that will enable them to stay ahead of the threats. For instance, knowing if an organization’s data has been leaked can help security analysts change the relevant credentials and secure their systems before an attack occurs.
Further, monitoring exchanges on dark web forums allows security personnel to gather threat intelligence. This enables them to gain insights into the operations of sophisticated adversaries and be warned of emerging threats.
Using threat intelligence platforms to analyze the threat data gathered from the dark web also enables organizations to defend themselves against attacks more effectively.
Finally, law enforcement agencies can access the dark web to detect illegal activity, such as weapon deals, drug distribution, and financial crimes. For instance, money laundering can be detected by correlating cryptocurrency wallet addresses with illicit activities. Law enforcement officials can also set up traps to capture criminals engaged in illegal transactions.
The deep web is largely secure and user-friendly. Accessing websites here is a safe, routine process. However, maintaining security procedures is critical even though these websites are legitimate.
As discussed above, user profiles on the deep web are home to valuable personal data to criminals. It is important to use strong, unique credentials for every account. A password management solution can be useful here.
Basic online hygiene can prevent security lapses when accessing the deep web. For instance, using an unprotected public network to pay your bills might lead to cybercriminals being able to capture your payment information.
It is also advisable for users to look for phishing scams, where criminals share communications that seemingly originate from a reputable source. Unwitting users then share sensitive personal information by falsely believing that these communications are legitimate.
Bottom line: Unlike accessing the dark web, which is fraught with security and legal risks, deep web security is a matter of common-sense best practices.
Summary
The dark web is a vast resource with many legitimate uses, yet it is home to criminal activities. The deep web on the other hand, is a normal aspect of the online experience for virtually every internet user.
As a sub-section of the deep web, the dark web shares numerous features. However, there are notable differences in the way it operates, its size, scope, access methodology, applications as well as its security.
Sorry, there were no replies found.